
The industrial management systems, manufacturing and providing utility services such as electricity, oil, water … are operated by electrical – electronic, mechanical, hydraulic and other specialized equipment. . Due to the nature of the industry, these systems are operated continuously 24/7, automatically and have self-control mechanism according to pre-set hypothetical situations. Therefore, these systems are normally operated and monitored by specialized computer systems called controllers and sensors. Integrated with management systems, they provide SCADA (Data Collection System and Surveillance Control Systems) solutions, enable efficient data collection and analysis, and help automate control of the devices. specialized equipment in the system such as pumps, valves and relays.
SCADA: Supervisory Control And Data Acquisition – Data Collection and Monitoring System
Used in systems requiring high levels of reliability, continuous operation in harsh industrial environments, not easy to replace and install, so equipment in SCADA solutions must ensure durability. sustainable and durable for a long time, from 5 years or even more than 10 years.
With their importance and influence on the community and society, public service providers, urban traffic control systems, have become targets of attack and have recently been hit by series of network breaches, data theft and denial of service … Of course, we get to know this most through Hollywood stories and movies, but it actually happened in real life.
In Vietnam, ostensibly, it’s hacker attacks and hijacking the airport screen display system. But really, does the customer database system of the airline still ensure safety and integrity?
With such reality, besides ensuring the continuous provision of social services, data integrity, accuracy in air / road traffic control, a prerequisite is that we concerns about the security of SCADA systems need to be thoroughly addressed, with long-term equipment, using devices, systems and technologies that are 5-10 years old. And the world technology is being researched, developed and applied at a tremendous speed. What an unequal war.
SCADA network characteristics and security requirements:
Although the design and manufacture of SCADA controllers as well as the management system installation device are according to the user’s specific requirements depending on the system requirements, it is still not separate from the fact that use on the platform. workstation platforms install a customized standard operating system (Windows / Linux or Unix), along with popular software applications, communication and login protocols.
Therefore, while it looks different, SCADA systems will have all kinds of problems such as conventional IT systems, vulnerabilities, differences between tested products, backdoors, lack of authentication and encryption. patched updates and weak password storage will allow attackers to gain access to the system. Thus the risk of equipment can cause them to hang or stop them and interfere with important processes controlled by them, such as opening and closing valves, disrupting the traffic control system.
However, by duty, the SCADA network is physically separated from the enterprise / organization’s IT networks, or uses the same IT network (LAN and WAN) but encrypts their SCADA network traffic on a single Shared infrastructure. And, both networks have an exchange to retrieve data information as well as send operational requests between them.
In addition to the element of being a network connected to the IT network, SCADA devices and networks have additional features that are different from those of IT devices and networks:
-
Installed in locations that are inconvenient for installation workers (towers, on oil rigs, operating robots, power / water / oil plants, traffic lights), are more environmentally required than IT systems usually (eg outdoors, extreme temperature, highly acidic / alkaline environment, shaking pulse) or specific input / output requirements.
-
Uses common operating systems, but customized / embedded to be compatible with the system, but with little regard for security.
-
The software is tailored to the availability and durability of the system, so it is rarely updated or patched regularly, due to limited access or fear of interruptions. for system upgrades.
- Use proprietary or special protocols like MODBUS, DNP3.
Security service providers with extensive experience in protecting IT networks against ever-increasing system threats, from operating system failures, application software vulnerabilities, or hardware-software to firmware incompatibility, continuous optimization, development of processes that allow systems to be built as close to operational levels safely.
The reuse of knowledge, continuous research, and application of technology developed over the years can build a safe system, at the same time save time and cost. This is only possible when the necessary condition is to understand and evaluate the difference between SCADA and the IT environment, before applying specific security practices and technologies as part of the solution.
Principles of designing security systems for SCADA networks
- Designing total security solutions for SCADA networks, as well as connecting SCADA and IT networks, need to meet both equipment and solutions, the main principles are as follows:
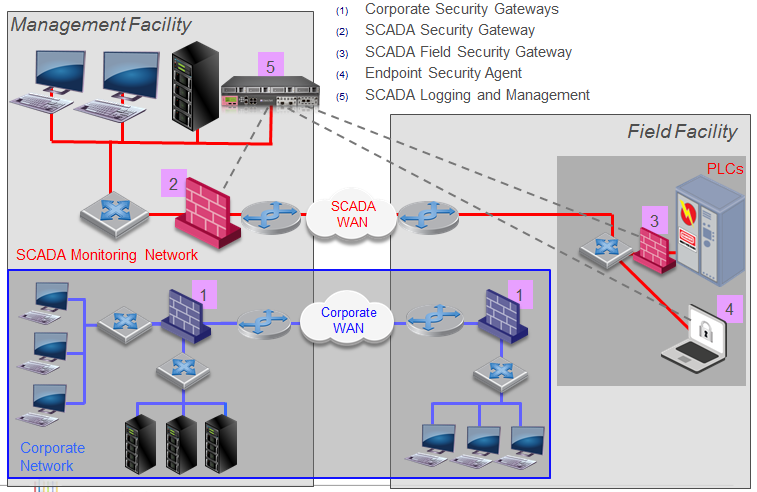
- There is physical separation between SCADA’s real-time operational controllers and other networks (Corporate Network – enterprise IT network, SCADA Monitoring Network – SCADA monitoring network).
- Put Gateway security devices at the connection between networks, ensuring that only traffic is authenticated and allowed in / out of the network. This validation must be performed on all communications, protocols, methods, queries and responses, and payloads by firewalls, application control, IPS and antivirus.
-
Use anti-bot attack solution to deal with malware that may have entered and resided in the device network.
-
Apply sandboxing technology (software virtualization) to help isolate / identify and handle malware embedded in application files such as Excel, Word, Power Point, PDF, EXE …
- Make sure all workstations used for management and maintenance are malware-free, and that the following requirements are observed:
- Use separate workstations for SCADA management software.
- With workstations operating in both IT, SCADA and Internet networks, there are clear policies for users, with software and machine configuration and need to monitor traffic / files and system load in real time. .
-
All workstations must be controlled by a number of endpoints including firewalls, application control, gateway control, communications authentication / encryption, IPS and antivirus.
Security solution for SCADA network

General security solution model proposed for SCADA and IT network of customers.
Security solutions include 2 main tasks:
- Provide security solution between SCADA network and related network (enterprise IT network, SCADA system monitoring network). Thus, at each gateway between networks, as well as in front of SCADA devices, there are devices to protect the network.
-
Security devices are designed to ensure operability in industrial environments. The main security features active on the device include: FW, IPS, application control, Identity Awareness, Antibot & Anti Virus, this allows legitimate traffic to be exchanged between different components of the system. SCADA, at the same time allows to detect bots in SCADA system (post-infection) and thereby prevent those connections from going out to the Internet.
Security devices should include:
- Firewall bảo vệ biên mạng SCADA
- Designed with security function for SCADA devices such as controller of stations, control cabinets …, depending on the importance of the device, Standalone or High Availability mode can be set.
-
The device is not only designed to operate in harsh industrial environments, but is also designed to provide comprehensive security support for SCADA systems. The device has a solid physical design. Dust, maximum temperature, humidity and vibration regulations must be observed to ensure physical durability.
-
Equipment needs to ensure extremely high MTBF (average time between failures) and highly reliable hard drive and fan accessories, ensuring long-term use with little maintenance, repair, or replacement. so.
- Firewall protects monitoring center network and power stations at operating levels L3.5 to L4.5. It has full security features and protects against threats to SCADA and related networks, and has a large throughput to ensure processing speed for control and operation management applications. To a great extent, this firewall is set to high priority High Availability, Cluster or Active-Standby.
 Centralized management equipment:
Centralized management equipment:
- Manage all firewall security devices, providing overall, unified management of the status, logs and security policies of all firewalls connecting on IT and SCADA networks to ensure consistency of policies, quick response to information security events and incidents.
-
Since the security of organizations consists of many layers, it is important to have a single view of all security incidents in one place. Standardizing and unifying security solutions can enable experts to be present in the organization and provide a better overview of security attitudes across security devices and security devices. IT system security and terminal computers.

